Blog
Switching Aspera HSTS from License Key to Entitlement
This article describes how to switch an existing High-Speed Transfer Server from a license key to an entitlement. …
Why is FTP Bad
Introduction In today’s rapidly evolving business world, organizations depend on seamless communication and collaboration. Whether it’s supporting a global workforce or communicating …
What Are The Risks of Cloud Computing?
Cloud computing is a service offering model that provides on-demand IT resources for organizations and individuals. In this model, users and organizations …
Aspera on Cloud Edition Comparison
Aspera on Cloud or AoC is a cloud-based hosted service that allows organizations to transfer files in a seamless, secure and fast …
Updating SSL Certificates in Aspera Web Applications
An important part of securing these web applications is to install an SSL/TLS Certificate that has been signed by a trusted Certificate …
Aspera Product Architecture
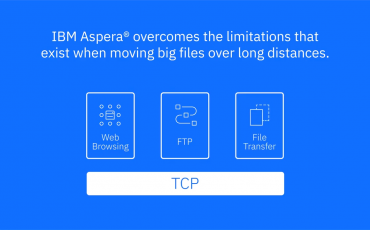
As we enter a more data-driven interconnected global economy, solutions built on FTP aren’t holding up. This is where new solutions such …
Aspera Technology (SDK, ASCP & More)
Aspera Technology Overview While many companies and academic institutions have tackled the WAN data movement problem, they have chosen to optimize or …
Secure File Transfer Alternatives to FTP
IBM’s Aspera patented data transfer protocol known as FASP or Fast and Secure Protocol stands out as one of the most well-adopted …
Frequently Asked Questions About Aspera
Solutions such as IBM’s Aspera utilize a patented file transfer protocol known as FASP or Fast and Secure Protocol to transfer files …
Aspera vs FTP
IBM Aspera is actually a faster alternative to FTP server software to reliably and securely transfer files. …
CORE Screener by 5th Kind
CORE Screener truly provides exceptional service to users through a blend of completely dependable security, extensive functionality, and a rather simple user …
Benefits of IBM Aspera Enterprise Tier Licensing
The IBM Aspera Enterprise licensing encompasses all of the core functionality of the IBM Aspera software with additional features and services that …
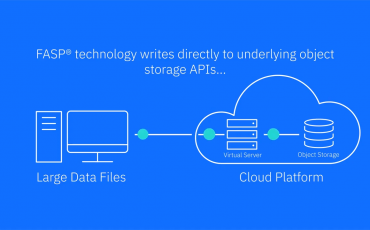
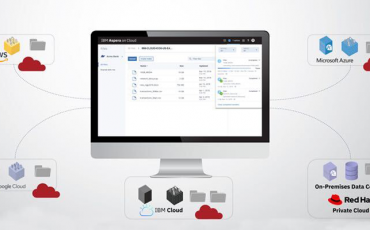
Aspera on Cloud Overview and Capabilities
The traditional data transfer practices simply do not suffice when attempting to seamlessly transfer and collaborate on data within a hybrid cloud …
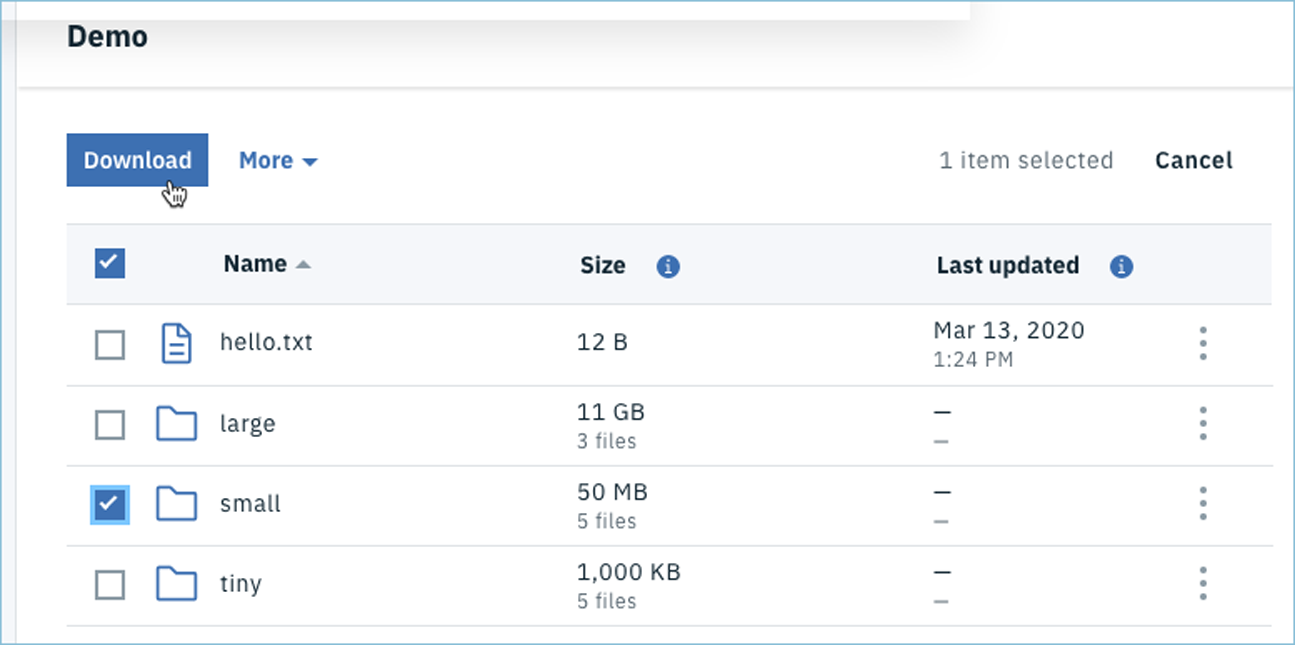
PacGenesis Blog: How to Start a Transfer with Aspera Connect
IBM Aspera Connect is a web application-based offering built on the Aspera transfer server that allows users to upload and download files …
What is Cybercrime?
Cybercrime is defined as any criminal activity that is committed using computers, networks, and the internet. There are thousands of crimes that …
Protecting Apps & Protecting Platforms from Piracy
The need for advanced privacy and security enhancements is due to ever-evolving cybersecurity threats through data exposure and data hacking. …
Protecting Apps & Platforms from Cybercriminals
We’re finding that as technological advancement accelerates and new unique applications and platforms help businesses grow, build revenue and break into new …
Cybersecurity for Apps & Cybersecurity for Platforms
At PacGenesis, we’ve partnered with vetted cybersecurity companies with decades of experience in digital platform and application security. Here are two of …
PacGenesis Analysis: Aspera vs Signiant vs Egnyte
In this brief, we will look at three technology-focused organizations who are providing solutions for organizations looking to adopt more modernized data …
IBM Aspera Connect Server Web Interface No Longer Supported
IBM Aspera High-Speed Transfer Server (HSTS) v4.0 was released in November 2020. This release contains many enhancements and fixes. HSTS v4.0 also …
IBM Aspera Support: Best Practices For Aspera Support
For companies and employees of companies who purchased IBM Aspera products, you’ll be able to access support through the following methods: …
IBM Aspera Orchestrator Capabilities
Aspera Orchestrator can direct, process, and redirect files with easy-to-use rules based on your organization’s workflows and using your IT infrastructure. …
Aspera Faspex vs. Aspera Shares: Use Case Comparison
In this article, we will discuss the value of IBM’s Aspera Faspex and IBM’s Aspera Shares, and provide a use case comparison …
What is Aspera FASP®?
Aspera is the fastest high-speed file transferring system on the market for sending large files or large volumes of files around the …
Coming Soon: 7-part Aspera Training Course
We here at PacGenesis are releasing a 7-part technical training series that will provide users with a comprehensive overview of the IBM …
How Does IBM Aspera Work?
IBM Aspera has become the software solution for sending big files at high-speed around the globe. It is based on the point-to-point …
Learn About Aspera Console Features and Functionalities
As we’re talking to organizations that are considering adopting IBM Aspera for high-speed file transfers, they’re understandably curious how much control their …
Your First Aspera HSTS Install
If you’re anything like me, you learn best by doing. So when I set out to learn Aspera many years ago, …
Cybersecurity Awareness Month Gives Businesses and Citizens Actionable Steps To Protect Themselves from Cybercriminals
October is Cybersecurity Awareness Month, and we’ve got actionable steps for you to take to protect your business and family from cybercriminals. …
Irdeto and IBM Team Up to Provide Best-in-Class, Pre-integrated Solution for Transferring Videos That Have Forensic Watermarking to Track Leaks
Learn about the new forensic watermarking integration from Irdeto and IBM Aspera to trace video content leaks. …
Disney and MGM Studios Executives Endorse PacGenesis
Leading Media & Entertainment Businesses Rely on Premier IBM Aspera Business Partner PacGenesis As They Use the World’s Fastest High-Speed File Transfer …
How to Use Irdeto to Protect Platforms and Apps from Piracy and Cybercriminals
If you are in the platform or app development business - such as the software industry, the gaming industry, or mobile app …
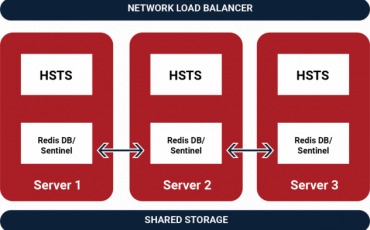
HSTS High Availability
We all know the story. You start with a single High Speed Transfer Server and a web app such as Shares or …
How Consumers Feel About Cybersecurity in the Midst of the COVID-19 Pandemic – And Why They Should be Worrying More
As a solutions provider that helps organizations implement cybersecurity solutions from Irdeto, we’re particularly interested in how Americans are viewing the threat …
What is the Maximum Speed of an Aspera Transfer?
Do you need to transfer files really quickly, as in, as quickly as possible? Do you need to send those files, which …
What Ports Does Aspera Use?
If you’re evaluating IBM’s Aspera for high-speed file transferring within your organization, you may be wondering what ports the solution uses. Don’t …
IBM Releases Aspera Orchestrator 4.0
Recently, IBM released an update, Aspera Orchestrator 4.0. As you know, Orchestrator is the complete automation platform that makes it easy for …
Aspera Licensing Models
IBM knows that every organization that uses Aspera is different, and has unique needs. That’s why they’ve created two flexible licensing models …
HIPAA Certified Software for Transfering Healthcare and Biotech Data The Fastest Way Possible
To solve both your file transfer and patient privacy needs, allow me to introduce you to IBM’s Aspera. Aspera is the world’s …
Using Aspera for High-speed Digital Asset and Creative File Transfers
Created by IBM, Aspera is the solution you’ve been looking for. Leveraging its patented FASP® technology, Aspera securely sends files across the …
Aspera Security Vulnerability
On April 24th, IBM announced what they are calling a Buffer Overflowvulnerability in the aspshell executable of Aspera. This vulnerability effects all …
Did You Know Video Content Transferred with Aspera Can be Watermarked with Irdeto Technology?
When you use IBM Aspera to send video files around the world using the fastest file transfer technology on the market, a …
Now That Collecting Retail Data is So Easy, IBM Aspera Makes Sharing it Faster Than Ever Before
From digital marketing assets to customer, store, and product data, retailers’ file-sharing needs have significantly increased in recent years. Maintaining a consistent …
Speed Up Oil and Gas Data Transfers and Workflows with IBM Aspera
Whether you’re trying to solve data transfer challenges between onshore and offshore operations, plants and globally distributed offices, or both, IBM’s Aspera …
All About IBM Aspera
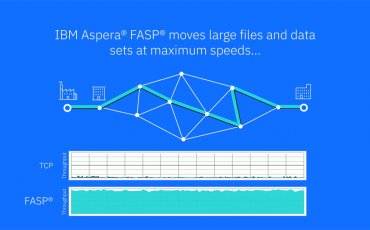
Aspera is the fastest way to move data. Rather than relying on TCP, the solution uses its own proprietary FASP technology to …
Why Aspera?
Read this blog post to learn why Aspera is the best solution for transferring large files, large volumes of files, and streaming …
Fix Central Access
All software needs to be updated at certain points in time. Aspera regularly releases updates to address issues and improve usability and …